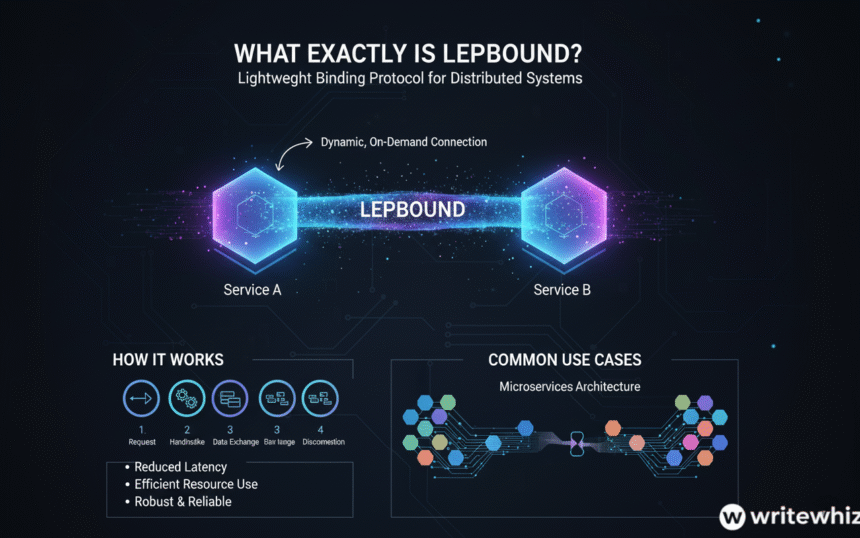
What Exactly Is Lepbound?
You’ve probably stumbled across the term “lepbound” and wondered what it means. This relatively new concept has been gaining attention in tech circles, yet many people still scratch their heads when they hear it. Lepbound refers to a specific binding protocol that connects lightweight execution processes within distributed computing environments. Think of it as a bridge that allows different software components to communicate efficiently without eating up your system resources.
The beauty of lepbound lies in its simplicity. Unlike traditional binding methods that require heavy overhead and complex configurations, this approach streamlines the entire process. Software developers appreciate how it reduces latency while maintaining robust connections between services. As our digital infrastructure grows more complex, solutions like lepbound become increasingly valuable for keeping everything running smoothly.
The Origins and Development of Lepbound
The concept emerged from the need to solve a persistent problem in distributed systems. Engineers noticed that conventional binding protocols were slowing down applications, especially when dealing with microservices architectures. They needed something lighter, faster, and more adaptable to modern computing demands. Through collaborative efforts in the open-source community, lepbound took shape as an answer to these challenges.
What started as an experimental project quickly gained traction among developers working with cloud-native applications. The protocol underwent several iterations, with each version addressing specific pain points reported by early adopters. By focusing on minimal resource consumption and maximum efficiency, the development team created something that genuinely improves how distributed systems operate. Today, lepbound continues to evolve based on real-world feedback and emerging technological requirements.
How Lepbound Works Behind the Scenes
Understanding the mechanics of lepbound helps you appreciate its value. The protocol operates by establishing temporary, lightweight connections between processes that need to share data or functionality. Instead of maintaining persistent connections that consume memory and processing power, lepbound creates these links on-demand and releases them when they’re no longer needed. This dynamic approach significantly reduces the overhead associated with inter-process communication.
The technical implementation relies on efficient message passing and smart resource allocation. When one component needs to communicate with another, lepbound handles the handshake process in milliseconds. It uses optimized data serialization methods that minimize the size of transmitted information without losing critical details. Furthermore, the protocol includes built-in error handling that prevents cascading failures when individual components experience issues. This resilience makes it particularly attractive for mission-critical applications where reliability matters.
Key Benefits That Set Lepbound Apart
Performance improvements stand out as the most obvious advantage. Applications using lepbound typically experience faster response times and reduced latency compared to those relying on traditional binding methods. Users notice the difference, especially in high-traffic scenarios where every millisecond counts. The protocol’s efficiency translates directly into better user experiences and higher satisfaction rates.
Beyond speed, lepbound offers excellent scalability characteristics. As your application grows and handles more requests, the protocol adapts without requiring significant reconfiguration. This flexibility saves development teams countless hours they would otherwise spend optimizing and tweaking their infrastructure. Additionally, the reduced resource consumption means you can handle more traffic with the same hardware, which translates to lower operational costs. Companies appreciate how these savings add up over time, making lepbound an economically smart choice.
Common Use Cases and Applications
Web applications represent one of the primary domains where lepbound shines. When you’re building a platform that needs to coordinate multiple services—authentication, database queries, external API calls, and more—this protocol keeps everything synchronized efficiently. E-commerce platforms particularly benefit from the speed improvements, as faster page loads and quicker checkout processes directly impact conversion rates.
Microservices architectures have also embraced lepbound enthusiastically. When you’re managing dozens or hundreds of small services that need to communicate with each other, traditional binding methods create bottlenecks. Lepbound eliminates these chokepoints by facilitating rapid, efficient communication between services. Internet of Things (IoT) applications present another compelling use case, where thousands of devices need to exchange data with central servers without overwhelming the network. The protocol’s lightweight nature makes it perfect for resource-constrained environments common in IoT deployments.
Technical Requirements and Prerequisites
Getting started with lepbound doesn’t require a complete infrastructure overhaul. Most modern programming languages offer libraries or packages that implement the protocol, making integration relatively straightforward. You’ll need a basic understanding of distributed systems concepts and familiarity with your chosen programming language’s networking capabilities. The learning curve remains manageable for developers with intermediate experience.
Your system should meet certain minimum specifications to take full advantage of lepbound’s capabilities. While the protocol itself is lightweight, you’ll want adequate memory and processing power to run your applications effectively. Network stability matters too, as any binding protocol relies on reliable connections between components. That said, lepbound handles network hiccups better than many alternatives, thanks to its built-in retry mechanisms and timeout management. Documentation and community resources have grown substantially, making it easier than ever to implement the protocol correctly.
Potential Challenges and Limitations
No technology comes without its tradeoffs, and lepbound is no exception. One challenge developers face involves debugging issues when things go wrong. Because the protocol creates temporary connections that disappear after use, tracing problems through your system can become tricky. You’ll need good logging practices and monitoring tools to track what’s happening behind the scenes. Without proper observability, identifying the root cause of failures becomes significantly harder.
Another consideration involves compatibility with legacy systems. If you’re working with older applications that weren’t designed with modern binding protocols in mind, integration might require additional wrapper code or middleware layers. This extra work doesn’t necessarily make lepbound unsuitable, but it does mean you’ll need to plan your migration strategy carefully. Additionally, while the community around lepbound continues to grow, it hasn’t reached the same maturity level as some longer-established protocols. You might occasionally encounter scenarios where you’re breaking new ground without extensive documentation to guide you.
Best Practices for Implementation
Success with lepbound starts with proper planning. Before implementing the protocol, map out your application’s architecture and identify which components will benefit most from its capabilities. Not every connection point needs lepbound—sometimes traditional methods work perfectly fine. Focus on areas where performance bottlenecks exist or where you anticipate scaling challenges down the road. This targeted approach prevents unnecessary complexity while maximizing benefits.
Testing thoroughly before deploying to production saves headaches later. Create realistic test scenarios that simulate actual usage patterns, including edge cases where things might fail. Pay special attention to how your system behaves under heavy load, as this reveals potential weaknesses in your implementation. Furthermore, implement comprehensive monitoring from day one. Track metrics like connection times, error rates, and resource usage to establish baselines. These measurements help you optimize performance and quickly identify when something goes wrong. Regular code reviews focused on lepbound-specific patterns ensure your team maintains consistency and follows established best practices.
The Future of Lepbound Technology
The trajectory for lepbound looks promising as more organizations recognize its value. Development efforts continue to refine the protocol, with upcoming versions promising even better performance and additional features. The community has proposed several enhancements, including improved security mechanisms and better support for emerging computing paradigms like edge computing. These improvements will expand the protocol’s applicability across even more use cases.
Industry adoption rates suggest lepbound will become increasingly mainstream over the next few years. Major technology companies have started evaluating it for their infrastructure, and some have already begun pilot implementations. As success stories accumulate and best practices solidify, we’ll likely see lepbound become a standard consideration in system design discussions. The protocol’s alignment with modern architectural trends—particularly serverless computing and containerized applications—positions it well for continued growth and relevance.
Conclusion: Making Sense of Lepbound
Lepbound represents a meaningful advancement in how distributed systems communicate. By prioritizing efficiency, scalability, and ease of implementation, it addresses real pain points that developers and organizations face daily. Whether you’re building a new application from scratch or looking to optimize an existing system, this protocol deserves consideration as part of your technical toolkit.
The key to success lies in understanding both its strengths and limitations. Lepbound excels in scenarios requiring fast, lightweight communication between services, particularly when dealing with modern cloud-native architectures. However, it requires thoughtful implementation and proper monitoring to realize its full potential. As the technology matures and the community grows, we’ll see even more innovative applications and refinements that push the boundaries of what’s possible. For developers willing to invest time in learning this protocol, the payoff comes in the form of more responsive, efficient, and scalable applications that serve users better.